Máy chủ Microsoft Exchange đang là mục tiêu của những kẻ phát tán phần mềm BlackCat Ransomware và có thông tin cho thấy tin tặc đang khai thác các lỗ hổng chưa được vá trên hệ thống để tạo ra phần mềm độc hại mã hóa tệp nói trên.
Người ta đã quan sát thấy rằng trong hơn hai trường hợp, tin tặc có thể đánh cắp thông tin đăng nhập và thông tin chuyển tiếp đến các máy chủ từ xa, để sử dụng dữ liệu đó cho việc tống tiền kép.

Tin tặc đầu tiên tấn công máy chủ nạn nhân trên một ghi chú ban đầu và sau đó được nhìn thấy đang triển khai các tải trọng BlackCat Ransomware trên toàn mạng thông qua PsExec.
Quy trình tấn công như sau:
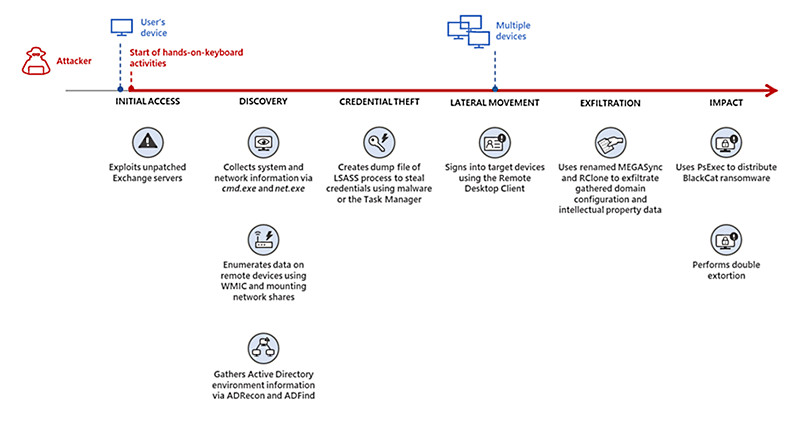
Microsoft đã lưu ý về tình hình và nghi ngờ rằng các vụ tấn công đang được thực hiện bởi một băng nhóm có liên quan đến ransomware như một hoạt động dịch vụ và đang yêu cầu tất cả các máy chủ trao đổi của họ tuân theo một lời khuyên được đưa ra vào ngày 14 tháng 3 để giảm thiểu các cuộc tấn công ProxyLogon.
Một trong số chúng, một nhóm tội phạm mạng có động cơ tài chính được theo dõi là FIN12, được biết đến với việc triển khai Ryuk, Conti và Hive ransomware trước đây trong các cuộc tấn công chủ yếu nhắm vào các tổ chức chăm sóc sức khỏe.
Công ty công nghệ này đang kêu gọi các tổ chức sử dụng một giải pháp toàn diện như Microsoft 365 Defender của riêng mình để bảo vệ các rủi ro liên quan đến các cuộc tấn công và đã đưa ra lời khuyên chi tiết để hạn chế các vấn đề phát sinh từ các cuộc tấn công mạng.
LƯU Ý- Các phiên bản Ransomware của BlackCat đang hoạt động trên cả phiên bản Windows và Linux và trong môi trường của VMware ESXi. Kể từ năm 2021, phần mềm độc hại mã hóa tệp tin còn được gọi là ransomware ALPHV đã được nhìn thấy yêu cầu 5 triệu đô la từ các nạn nhân của nó.
Phương Nguyễn dịch
Nguồn https://www.cybersecurity-insiders.com/blackcat-ransomware-is-being-induced-into-microsoft-exchange-servers